As you may already know, you can use Azure AD Conditional Access to secure access to your applications.
Well, good news as you can now also use Conditional Access with your Azure AD B2C (Business to Consumer) tenant to help you address user risks when accessing your B2C applications.
While you may already know the Azure AD Conditional Access, the Azure AD B2C Conditional Access has few differences:
- Security Center isn’t available in Azure AD B2C
- Identity Protection and Conditional Access aren’t supported for ROPC server-to-server flows in Azure AD B2C tenants
- Identity Protection risk detections are available for local B2C accounts only, and not for social identities like Google or Facebook
- Conditional Access device compliance feature isn’t available in Azure AD B2C tenants
From a licensing perspective, you need to have either Azure AD P1 to create policies based on location, application, user or group based or Azure AD P2 to also take advantage of the risky sing-in policies.
The first thing to take advantage of the Conditional Access in your Azure AD B2C is to turn off the Security defaults.
Connect to your Azure AD portal (https://aad.portal.azure.com/) and switch to your Azure AD B2C directory and access the Azure AD B2C properties to turn off the Security defaults
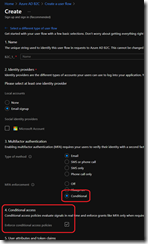
Then you can access the Security\Conditional Access blade to configure your policy/policies
You can then add the policy/policies to your user flows; your user flow template must not be a legacy one but a recommended one