As you know, Azure Security Center (ASC) is your one stop shop helping you maintain and improve your secure posture in Azure (including your on-premises workloads too if onboarded).
As you also know, ASC provides a recommendation (and report) for ensuring your virtual machines have an endpoint protection solution installed and healthy. This recommendation is unfortunately limited to specific solutions (you can get the list here https://docs.microsoft.com/en-us/azure/security-center/security-center-services?tabs=features-windows#endpoint-supported).
This means if you use any other endpoint protection solution, the recommendation will be fired as ASC is not able to properly detect your endpoint protection product.
Well, good news, you can now customize it to include your specific protection product.
The customization involves the use of a guest configuration policy (using DSC – Desired State Configuration).
To start customizing the endpoint protection recommendation, you need to download the AzureGuestPolicyHelper module to then create the policy package to be uploaded.
Connect to GitHub to download the module artifacts from https://github.com/Azure/Azure-Security-Center/tree/master/Remediation%20scripts/Customize%20Endpoint%20Protection%20Recommendation
Then copy the content of the Modules folder to your PowerShell modules folder (C:Program FilesWindowsPowerShellModules)
Now you can customize the parameter file (EPAntivirusStatus.Params.psd1 located in C:Program FilesWindowsPowerShellModulesEndPointProtectionDSCAzureGuestConfigurationPolicyParameterFiles) to set your endpoint protection solution.
A sample is shown below; you can use wildcard, like symantec*
@(
@{
Name = ‘AntivirusName’
DisplayName = ‘Antivirus Name’
Description = “Name of the Antivirus Software to monitor.”
ResourceType = “EPAntivirusStatus”
ResourceId = ‘AV’
ResourcePropertyName = “AntivirusName”
DefaultValue = ‘Windows Defender’
AllowedValues = @(‘Avast’,’Windows Defender’,’CrowdStrike’,’Sentinel One’)
}
)
Then connect to your Azure portal (https://portal.azure.com) to Deploy the prerequisites to enable Guest Configuration using a policy
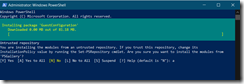
Then innstall the PowerShell modules for Guest Configuration, Azure PowerShell modules (just for the first time if this is not yet installed) and load the EndPoint Protection DSC modules
Install-Module -Name GuestConfiguration
Install-Module -Name Az
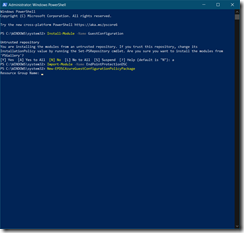
Import-Module -Name EndPointProtectionDSC
Then using the below command you will define the DSC package settings
New-EPDSCAzureGuestConfigurationPolicyPackage
This will request you to sign in to your Azure portal and then request for a
- Resource Group Name
- Resource Group Location – you can use the command Get-AzLocation to get the location code – like australiaeast for Australia East)
- Storage Container Name
- Storage account name
- Storage SKU name (see below)
Storage account SKU:
- Standard_LRS. Locally-redundant storage
- Standard_ZRS. Zone-redundant storage
- Standard_GRS. Geo-redundant storage
- Standard_RAGRS. Read access geo-redundant storage
- Premium_LRS. Premium locally-redundant storage
to save the guest configuration package; if the resource group and/or storage account do not exist, they will be created.
If you are using an existing storage account/container, the access policy must be set to Container (anonymous read access).
The MOF package is being generated and published to the container you have defined.
Then once the DSC package is published to your storage account you can define the Azure Policy for checking for endpoint protection.
Logon to your Azure portal (https://portal.azure.com) and access the Policy blade to deploy/assign the Monitor Antivirus initiative; when deploying the initiative you will then define the antivirus name as parameter – ensure you have added the antivirus name in the AllowedValues (see above)
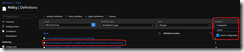
This will not (yet) update your Azure Security Center recommendations. To update your Azure Security Center recommendations, you need to edit the Security CenterSecurity Policy by accessing the Security CenterSecurity Policy blade to add the custom initiative
Now you are done, you have customized your ASC recommendation for endpoint protection.

![image_thumb[1] image_thumb[1]](https://www.cubesys.com.au/wp-content/uploads/2020/10/image_thumb1_thumb-270.png)
![image_thumb[2] image_thumb[2]](https://www.cubesys.com.au/wp-content/uploads/2020/10/image_thumb2_thumb-208.png)
![image_thumb[3] image_thumb[3]](https://www.cubesys.com.au/wp-content/uploads/2020/10/image_thumb3_thumb-162.png)
![image_thumb[4] image_thumb[4]](https://www.cubesys.com.au/wp-content/uploads/2020/10/image_thumb4_thumb-126.png)
![image_thumb[5] image_thumb[5]](https://www.cubesys.com.au/wp-content/uploads/2020/10/image_thumb5_thumb-84.png)
![image_thumb[6] image_thumb[6]](https://www.cubesys.com.au/wp-content/uploads/2020/10/image_thumb6_thumb-67.png)
![image_thumb[8] image_thumb[8]](https://www.cubesys.com.au/wp-content/uploads/2020/10/image_thumb8_thumb-38.png)
![image_thumb[7] image_thumb[7]](https://www.cubesys.com.au/wp-content/uploads/2020/10/image_thumb7_thumb-49.png)
![image_thumb[9] image_thumb[9]](https://www.cubesys.com.au/wp-content/uploads/2020/10/image_thumb9_thumb-26.png)