As you know, you can use access keys to access Azure Storage Account content (Blob, Table, File…).
While this is helpful this also implies some security risk when using public endpoints.
Well, good news, you can now disable account access keys on storage account to use Azure AD authentication instead.
IMPORTANT if you disable account access keys, you will not be able to access Azure Files or Table storage as they do not support (yet?) Azure AD authentication.
It is highly recommended to review access type on the storage account before turning of the access keys.
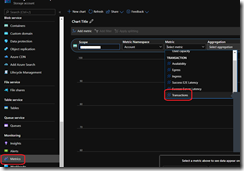
You can review how your storage account is access using the Transactions metric with the Sum aggregation for the storage account.
Then use the Authentication filter to identify if account keys are used using the values Account key and SAS
If you have data back, you can get more information to identify what is using SAS using the storage account Diagnostic and Log Analytics.
Enable the diagnostic settings to save logs in the Log Analytics workspace by accessing the Diagnostics blade for the storage account
Then you can query the log using KQL
StorageBlobLogs
| where AuthenticationType in (“AccountKey”, “SAS”) and TimeGenerated > ago(7d)
| summarize count() by CallerIpAddress, UserAgentHeader, AccountName
| top 10 by count_ desc
Once you have reviewed how your storage account is accessed, you can turn off the access keys (if possible) by accessing the storage account Configuration blade

![image_thumb[2] image_thumb2_thumb-227-1656636](/wp-content/uploads/2021/02/image_thumb2_thumb-227-1656636.png)
![image_thumb[4] image_thumb4_thumb-135-7120977](/wp-content/uploads/2021/02/image_thumb4_thumb-135-7120977.png)
![image_thumb[5] image_thumb5_thumb-90-3509364](/wp-content/uploads/2021/02/image_thumb5_thumb-90-3509364.png)
![image_thumb[6] image_thumb6_thumb-72-5303332](/wp-content/uploads/2021/02/image_thumb6_thumb-72-5303332.png)