After releasing a Power BI dashboard to follow up on the evolution of your Azure Secure Score (see https://t.co/U1I15FSuBP), you can now get an email notification if your Secure Score is reducing.
The playbook is available for deployment in the Azure Security Center Github repository here https://github.com/Azure/Azure-Security-Center/tree/master/Secure%20Score/Secure%20Score%20Reduction%20Alerts
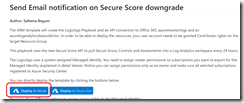
Connect to the above URL and use the Deploy to Azure button
Then you may be asked to authenticate against your Azure tenant.
Once authenticated, fill up the deployment details as below:
- Select the subscription where the playbook will be deployed
- As well as the resource group
- The region will be set automatically based on the above selection
- Provide the Log Analytics name, resource group and subscription ID
- Update (if needed) the frequency of reviewing the Secure Score and the percentage threshold reduction (meaning if the Secure Score reduces by x%)
- The notification email
Now you can complete the deployment
A Logic App called Send-SecureScoreReductionAlert with 2 API Connection called office365 and azuremonitorlogs been deployed.
You then need to grant Reader permission to the subscription(s) you want to get monitored for Secure Score reduction by accessing the Subscription Access Control blade
Then select the Reader role to be assigned to a Logic App and then select the Send-SecureScoreReductionAlert
Then go back to the resource group where the playbook has been deployed to edit the office365 API connection
Access the Edit API connection and then hit the blue ribbon to Authorize the connection; an authentication prompt may appear to ask you to sign in
You should then see a blue notification on top if the authorization has been successful; you can now save the modification
Repeat the same with the other API connection azuremonitorlogs
You can review above operations has been successful by accessing the Send-SecureScoreReductionAlert Logic app and then looking at the Run query and list results action available within the For Each loop using the Logic app designer blade; you should see the Connected to azuremonitorlogs information
Then you can force an initial run using the Run Trigger
Then if the reduction threshold is reached you will get the following type of notification

![image_thumb[1] image_thumb[1]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb1_thumb-234.png)
![image_thumb[3] image_thumb[3]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb3_thumb-143.png)
![image_thumb[4] image_thumb[4]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb4_thumb-114.png)
![image_thumb[5] image_thumb[5]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb5_thumb-73.png)
![image_thumb[7] image_thumb[7]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb7_thumb-45.png)
![image_thumb[8] image_thumb[8]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb8_thumb-34.png)
![image_thumb[11] image_thumb[11]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb11_thumb-22.png)
![image_thumb[12] image_thumb[12]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb12_thumb-12.png)
![image_thumb[13] image_thumb[13]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb13_thumb-9.png)
![image_thumb[14] image_thumb[14]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb14_thumb-4.png)
![image_thumb[15] image_thumb[15]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb15_thumb-6.png)
![image_thumb[16] image_thumb[16]](https://www.cubesys.com.au/wp-content/uploads/2020/08/image_thumb16_thumb-4.png)