As you know, Key Vault lets you save secrets, certificates or keys in a secure way to then allows you to use it either with automation or simply as a ‘user vault’.
You also know that access to the Key Vault is managed by assigning access policies, defining who can access and do what.
Well, good news, you can now use Role Based Access Control (RBAC) to set the Key Vault access policies.
With this new capability, you also have new RBAC roles available:
| Role | Description |
| Key Vault Administrator | Perform all data plane operations on a key vault and all objects in it, including certificates, keys, and secrets. Cannot manage key vault resources or manage role assignments |
| Key Vault Certificates Officer | Perform any action on the certificates of a key vault, except manage permissions |
| Key Vault Crypto Officer | Perform any action on the keys of a key vault, except manage permissions |
| Key Vault Crypto Service Encryption | Read metadata of keys and perform wrap/unwrap operations |
| Key Vault Crypto User | Read metadata of key vaults and its certificates, keys, and secrets. Cannot read sensitive values such as secret contents or key material |
| Key Vault Secrets Officer | Perform any action on the secrets of a key vault, except manage permissions |
| Key Vault Secrets User | Read secret contents |
| Key Vault Contributor | Manage Key Vaults. Do not have access to keys, secrets or certificates |
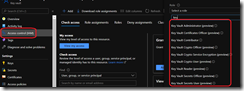
To start using RBAC to grant access to Key Vault, logon to you Azure portal (https://portal.azure.com/) and access your Key Vault
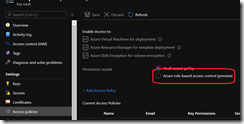
Then access the Access policies blade to enable the use of RBAC
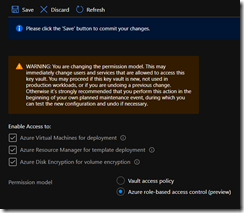
NOTE switching to RBAC may result of access being lost. You have to plan when you are going to perform the switch to avoid/limit service disruption
Once you have switch to the Azure role-based access control mode and save the change you can now use the Access control (IAM) blade to grant users/groups/service principal/managed identity the appropriate role