As you know, Office 365 comes with a bunch of security capabilities to help you protect your users and your IP’s as well as helping your company staying compliant with regulation.
That said this is not easy to detect bad activities from internal users – either done on purpose or by mistake – such as downloading lot of internal documentation and then resign.
To help you identifying such thing and take appropriate actions, Microsoft has introduce an Insider Risk Management capability to Office 365 Compliance.
This comes with any Office 365 E5 subscriptions, or the Microsoft 365 E5 Compliance add-on.
Insider Risk Management is helping you minimizing internal risks by detecting, investigating and taking action on malicious or inadvertent activities.
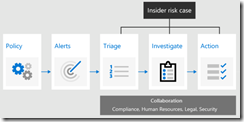
The principles of Insider Risk Management follow a ‘classic’ automated investigation workflow as below
- Create policies
- Alerts when suspect activities occur
- Investigator triage and review alerts
- Action can then be taken if required
When implementing Insider Risk Management policies, it is highly recommended to involve all teams which are going to take part of this workflow – legal, HR, compliance, IT security.
To start using this new capability, you need first to logon to the ‘old’ Compliance portal (https://protection.office.com/) using a global administrator account to grant Insider Risk Management permissions – you may need to create additional roles to grant the required permissions listed in the table below
| Role | Permissions |
| Insider Risk Management Administrator |
Create, read, update, and delete insider risk management policies |
| Insider Risk Management Analysts | Access to all insider risk management alerts, cases, and notices |
| Insider Risk Management Investigators | Access to all insider risk management alerts, cases, notices, and the Content Explorer for all cases |
| Insider Risk Management Viewer | View-only access to all insider risk management alerts, cases, notices, and the Content Explorer for all cases |
You can also connect the Insider Risk Management with your HR system (see https://docs.microsoft.com/en-us/microsoft-365/compliance/import-hr-data) to help detecting bad behaviour before resignation.
Once permission has been granted, you can now access the new Compliance portal (https://compliance.microsoft.com/) and access the Insider risk management blade – you may need to click the Show all link
Then go to the Policies tab to create policies – Insider Risk Management comes with predefined rules – more may come in future depending of customers feedbacks and new scenario being identified
- Departing users theft – requires the HR connector to be implemented
- Data leaks – requires DLP policies in place for signal detection
- Offensive language
When creating policy you have to identify to which users/groups to apply; you may create different policies to apply to different users/groups.
Then you have to define the location and/or sensitivity of the information
Once you have set your policies, Office 365 will start looking at the signals and start reporting activities.
You can create investigation cases directly from the dashboard to start deep investigation on activity.
You will have access to activities history for identified users, helping you defining if the behaviour is an adverted action or not.

![image_thumb[1] image_thumb[1]](https://www.cubesys.com.au/wp-content/uploads/2020/02/image_thumb1_thumb-98.png)
![image_thumb[2] image_thumb[2]](https://www.cubesys.com.au/wp-content/uploads/2020/02/image_thumb2_thumb-76.png)
![image_thumb[3] image_thumb[3]](https://www.cubesys.com.au/wp-content/uploads/2020/02/image_thumb3_thumb-62.png)
![image_thumb[4] image_thumb[4]](https://www.cubesys.com.au/wp-content/uploads/2020/02/image_thumb4_thumb-49.png)
![image_thumb[5] image_thumb[5]](https://www.cubesys.com.au/wp-content/uploads/2020/02/image_thumb5_thumb-31.png)
![image_thumb[6] image_thumb[6]](https://www.cubesys.com.au/wp-content/uploads/2020/02/image_thumb6_thumb-29.png)
![image_thumb[7] image_thumb[7]](https://www.cubesys.com.au/wp-content/uploads/2020/02/image_thumb7_thumb-23.png)
![image_thumb[8] image_thumb[8]](https://www.cubesys.com.au/wp-content/uploads/2020/02/image_thumb8_thumb-20.png)
![image_thumb[9] image_thumb[9]](https://www.cubesys.com.au/wp-content/uploads/2020/02/image_thumb9_thumb-10.png)